👉October Answers and Trivia
👉September Answers and Trivia
👉August Answers and Trivia
👉July Answers and Trivia
👉Jun Answers and Trivia
👉May Answers and Trivia
👉April Answers and Trivia
👉March Answers and Trivia
👉February Answers and Trivia
👉January Answers and Trivia
XENEA Wallet features a Daily Quiz that enhances user engagement while offering a fun and gamified way to learn about Web3 and the Xenea ecosystem.
Although many kind individuals are sharing answers on X (formerly Twitter), it feels like the quiz is turning into a game of simply picking the right answer without understanding the questions. To address this, this article will provide not only the answers to XENEA Wallet’s Daily Quiz but also the reasoning behind them and additional insights. By leveraging XENEA Wallet NAVI (ChatGPT), we aim to make the experience more informative and meaningful.
It takes less than a minute, so bookmark this page and check back daily! 😊
Start Your Journey with XENEA Wallet Today!
XENEA Wallet is an innovative app that makes exploring the world of Web3 both fun and rewarding! Complete simple missions, claim daily bonuses, and earn rewards while learning about the future of digital technology.
With cutting-edge security and unparalleled convenience, XENEA Wallet offers you the chance to participate in future airdrops and mining opportunities. Simply download the app to begin your new digital experience!
New users can start with 1,000 gems by signing up with the invite code below!
1️⃣ Download the app
2️⃣ Enter the invite code: h3dYzHejPI
3️⃣ Sign up with your Google or Apple account
Enjoy the exciting world of XENEA Wallet!
Please refer to the following page for information on how to earn Gems.
How many days does it take to earn 10,000 gems and start automatic mining with the XENEA Wallet?
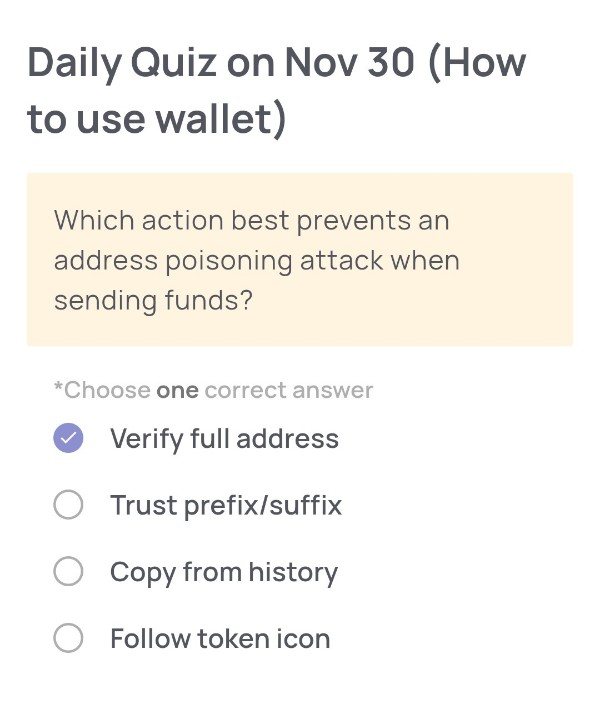
Daily Quiz on November 30
(How to use wallet)
🟢Quiz Questions:
Which action best prevents an address poisoning attack when sending funds?
🟢Choose one correct answer:
・Verify full address
・Trust prefix/suffix
・Copy from history
・Follow token icon
🟢Answer:
Verify full address
🟢Reason for choosing this answer:
Address poisoning attacks work by sending a small transaction from a wallet address that looks almost identical to the real one—same prefix and suffix—hoping users blindly copy it from transaction history.
Therefore, relying on prefix/suffix, history, or icons is unsafe.
The only reliable method to avoid sending funds to a fake address is to verify the entire address carefully, not just part of it.
🟢 Trivia:
Address poisoning became common on networks like Ethereum because attackers exploit human behavior: users often copy previous addresses instead of checking thoroughly.
Modern wallets, including XENEA Wallet, are improving UI/UX to reduce this attack risk—but the strongest protection is still user verification of the full address before sending funds.
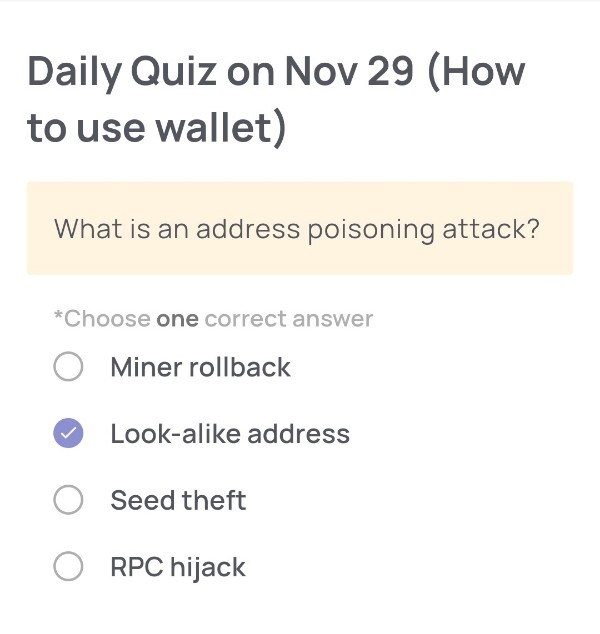
Daily Quiz on November 29
(How to use wallet)
🟢Quiz Questions:
What is an address poisoning attack?
🟢Choose one correct answer:
・Miner rollback
・Look-alike address
・Seed theft
・RPC hijack
🟢Answer:
Look-alike address
🟢Reason for choosing this answer:
An address poisoning attack happens when an attacker sends a tiny or fake transaction using a look-alike wallet address—one that closely resembles the victim’s real address.
The goal is to trick the user into copying the wrong address from their transaction history and accidentally sending funds to the attacker.
Because it relies on visual similarity, “Look-alike address” is the correct choice.
🟢Trivia:
This type of scam has become more common as users rely heavily on copy-and-paste from transaction history.
Best practice: Always verify the entire address—check the first 6 and last 6 characters—before sending tokens.
Modern wallets like XENEA Wallet, which uses a seedless/keyless MPC architecture, protect your keys but cannot prevent user mistakes, so careful confirmation is essential.
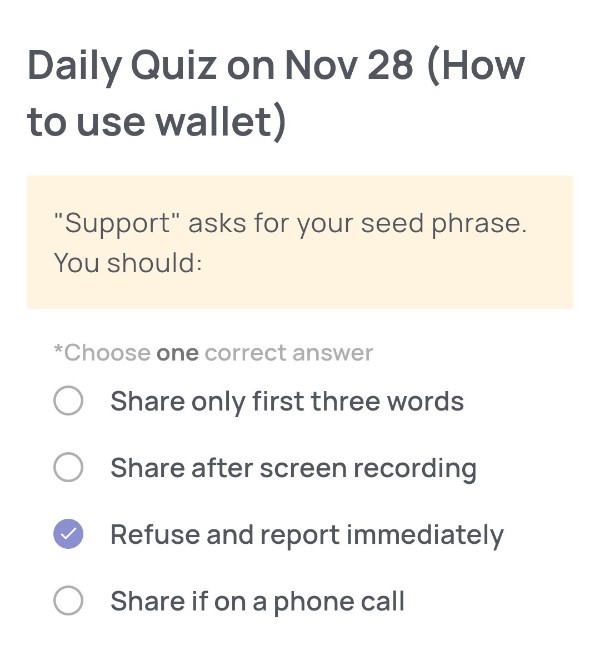
Daily Quiz on November 28
(How to Use Wallet)
🟢Quiz Questions:
“Support” asks for your seed phrase. You should:
🟢Choose one correct answer:
・Share only first three words
・Share after screen recording
・Refuse and report immediately
・Share if on a phone call
🟢Answer:
Refuse and report immediately
🟢Reason for choosing this answer:
A legitimate support team—whether for XENEA Wallet or any other Web3 wallet—will never ask for your seed phrase, private key, or security answers.
These credentials give full control over your assets, and sharing them enables irreversible theft.
Therefore, the only correct and safe response is to refuse and immediately report the request as fraud.
Even more importantly, XENEA Wallet uses a seedless, keyless MPC-based security architecture, meaning users do not even have a seed phrase to share. This makes any request for a seed phrase an instant red flag indicating a scam.
🟢Trivia:
In traditional wallets, seed phrases are the single point of failure—once leaked, assets are unrecoverable.
XENEA Wallet solves this risk through an internationally patented key-splitting MPC system where private keys are divided and stored across multiple anonymous nodes rather than with the user.
This eliminates the need for a seed phrase altogether and dramatically improves security.
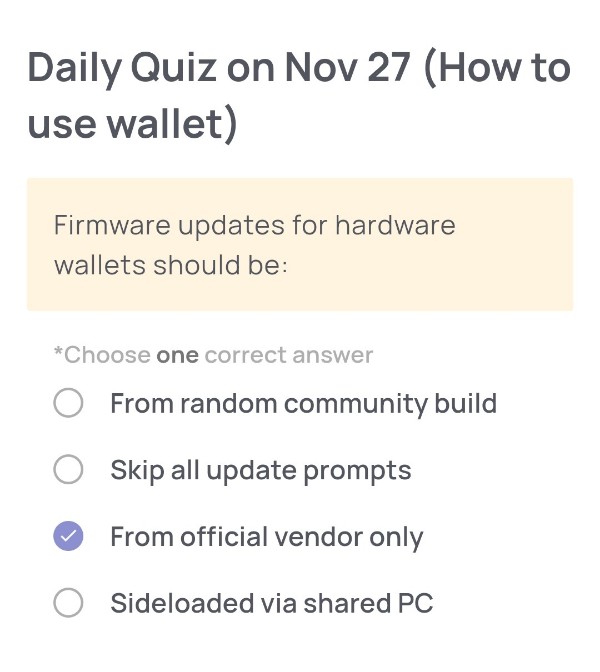
Daily Quiz on November 27
(How to use wallet)
🟢Quiz Questions:
Firmware updates for hardware wallets should be:
🟢Choose one correct answer:
・From random community build
・Skip all update prompts
・From official vendor only
・Sideloaded via shared PC
🟢Answer:
From official vendor only
🟢Reason for choosing this answer:
Firmware is the core software that controls a hardware wallet’s security functions, such as private-key protection and transaction signing.
Installing firmware from unofficial sources (community builds, sideloaded files, shared PCs, etc.) exposes the device to malware, backdoors, or unauthorized modifications that can compromise your assets.
Therefore, firmware must always be updated directly from the official vendor to ensure authenticity, integrity, and verified security.
🟢Trivia:
Most reputable hardware wallet manufacturers digitally sign their firmware. This means the device will only install updates that match the vendor’s cryptographic signature. This protects users from malicious firmware—even if someone tries to modify or replace the update file.
Daily Quiz on November 26
(How to use wallet)
🟢Quiz Questions:
Safer way to scan payment QR codes?
🟢Choose one correct answer:
・Auto-fill any amount
・Accept edited addresses
・Disable address checksum
・Verify source authenticity
🟢Answer:
Verify source authenticity
🟢Reason for choosing this answer:
Verifying the authenticity of the QR code source is the safest practice because QR codes used for crypto payments can be easily spoofed or replaced by malicious actors. Scanning only trusted and confirmed sources—such as the official merchant, the verified sender, or a secure platform—protects you from redirected payments, modified wallet addresses, and phishing attempts.
The other options intentionally weaken security and increase the risk of unauthorized transfers.
🟢Trivia:
Many modern crypto wallets, including Xenea Wallet, automatically perform checks such as address validation, checksum verification, and scam detection. However, human confirmation—ensuring the QR code comes from a legitimate source—remains the strongest first line of defense against fraud.
Daily Quiz on November 25
(How to use wallet)
🟢Quiz Questions:
Before sending a large transfer, you should:
🟢Choose one correct answer:
・Maximize gas to hurry
・Disable nonce control
・Export your private key
・Send a small test first
🟢Answer:
Send a small test first
🟢Reason for choosing this answer:
Sending a small test transaction before making a large transfer is one of the safest practices when using any crypto wallet.
It helps you confirm:
・The destination address is correct
・The network is functioning normally
・The wallet settings (gas, chain selection, etc.) are working as expected
This minimizes the risk of losing a large amount of assets due to mistakes or unexpected errors.
🟢Trivia:
Even advanced users and institutions regularly perform “test sends,” especially when moving large holdings or interacting with new wallets, exchanges, or smart contracts.
Because blockchain transactions are irreversible, this simple habit has prevented countless losses caused by typos, phishing, or misconfigured networks.
Daily Quiz on November 24
(How to use wallet)
🟢Quiz Questions:
How to handle dusting attacks?
🟢 Choose one correct answer:
・Swap dust for stablecoins
・Send dust to yourself
・Do not move the dust
・Approve dust for spending
🟢Answer:
Do not move the dust
🟢Reason for choosing this answer:
A dusting attack is when an attacker sends tiny amounts of crypto (“dust”) to your wallet to track your activity and deanonymize you.
If you move or interact with the dust, your address clustering becomes much easier for the attacker.
Therefore, the safest option is to do nothing—leave the dust untouched so the attacker cannot connect your transactions together.
🟢Trivia:
Dusting attacks became widely known in the Bitcoin and Litecoin ecosystems, but they can happen on any public blockchain.
Modern wallets often include “hide dust” or “anti-dust” protection features to prevent users from accidentally spending dust and exposing their transaction history.
Daily Quiz on November 23
(How to use wallet)
🟢Quiz Question:
What is address poisoning?
🟢Choose one correct answer:
・Look-alike address trickery
・Free airdrop distribution
・Node memory overflow bug
・Wallet theming feature set
🟢Answer:
Look-alike address trickery
🟢Reason for choosing this answer:
Address poisoning is a common crypto scam in which attackers send small transactions from a wallet address that looks almost identical to the user’s real address. The goal is to “poison” the transaction history so that the user accidentally copies the fake address when sending funds later.
Because this technique relies on visual similarity (e.g., same beginning and ending characters), the correct choice is “Look-alike address trickery.”
🟢 Trivia:
Address poisoning became popular because modern wallets often display only the first and last few characters of a long wallet address. This makes it easier for attackers to craft look-alike addresses.
To stay safe, always double-check the full address before sending funds and avoid copying addresses from your transaction history without verifying them first. Many advanced wallets, including modern MPC-based seedless wallets like XENEA Wallet, help reduce user error by improving security flows—but users should still remain cautious.
Daily Quiz on November 22
(How to use wallet)
🟢Quiz Questions:
Good practice for seed backups?
🟢Choose one correct answer:
・One photo in phone gallery
・Offline, redundant, protected
・Save in public cloud notes
・Send to work email thread
🟢 Answer:
Offline, redundant, protected
🟢 Reason for choosing this answer:
Storing your seed phrase (or recovery backup) offline, in multiple redundant (i.e., more than one) secure locations, and protecting it (e.g., with physical copies, safe storage) is the best practice. Storing it as a photo in your phone gallery, saving it in public cloud notes, or sending it via work email all expose it to online access or potential compromise, which defeats the purpose of secure backup. For example: one photo on your phone could be lost or hacked, cloud notes can be accessed by malicious actors, and email threads can be breached or accidentally forwarded.
🟢 Trivia:
In the context of the Xenea Wallet, it’s emphasized that a recovery phrase is the only way to restore your wallet if you lose access. According to a review, “Best practice is to store this phrase offline in at least two secure locations, never share it with anyone, and avoid syncing it to cloud storage where accounts can be phished or compromised.
Daily Quiz on November 21
(How to use wallet)
🟢Quiz Questions:
What does MPC primarily do?
🟢Choose one correct answer:
・Compress on-chain storage
・Split signing across parties
・Boost wallet UI themes
・Replace seed phrases fully
🟢Answer:
Split signing across parties
🟢Reason for choosing this answer:
MPC (Multi-Party Computation) is a cryptographic method that divides a private key into multiple parts and allows multiple parties (or nodes) to cooperatively perform a signature without ever reconstructing the full key in one place. This significantly strengthens security by ensuring no single device or server holds the complete private key—a key reason XENEA Wallet’s patented architecture uses MPC-based technology.
🟢Trivia:
MPC is often combined with techniques like Shamir Secret Sharing, which also splits a secret into multiple components stored in different locations. Even if one share is compromised, attackers cannot obtain the full key. This approach enhances both security and resilience, making MPC a popular choice in modern seedless, keyless wallets.
Daily Quiz on November 20
(How to use wallet)
🟢Quiz Questions:
Main benefit of multisig treasury setup?
🟢Choose one correct answer:
・Shared control for moves
・Faster block confirmations
・Free cross-chain transfers
・Higher staking rewards
🟢Answer:
Shared control for moves
🟢Reason for choosing this answer:
A multisig (multi-signature) treasury requires multiple authorized parties to approve a transaction before funds can be moved. This design prevents unilateral withdrawals, reduces internal risk, and ensures a higher level of security and accountability. The other options—faster confirmations, free cross-chain transfers, or increased staking rewards—are not benefits provided by multisig setups.
🟢Trivia:
Multisig wallets are widely used by DAOs, project treasuries, and organizations managing shared funds. They work similarly to a joint bank account, but with cryptographic enforcement. Even if one key is compromised, attackers cannot move funds without the remaining signatures. This makes multisig one of the most effective security layers in Web3 treasury management.
Daily Quiz on November 19
(How to use wallet)
🟢Quiz Questions:
Why are unlimited token approvals risky?
🟢Choose one correct answer:
・They delete past history
・They reset nonces often
・They increase gas fees
・DApp can drain tokens
🟢Answer:
DApp can drain tokens
🟢Reason for choosing this answer:
Unlimited token approvals mean you’re giving permission to a smart contract or DApp to spend any amount of a particular token from your wallet, with no fixed limit. If that DApp is malicious, compromised, or has a vulnerability, it can use that unlimited approval to withdraw all your tokens of that type from your wallet.
The other options don’t describe the core risk: unlimited approvals don’t inherently delete history, reset nonces, or necessarily increase gas fees (though revoking approvals may cost gas). The key danger is where the permissions allow full token drain.
🟢Trivia:
Here are two interesting nuggets:
・According to Coinbase, more than US$405 million has been stolen through exploits involving unlimited token approvals.
・A good safety practice is to grant only what you need (a fixed small allowance rather than unlimited), and to regularly revoke approvals for DApps you no longer use.
Daily Quiz on November 18
(How to use wallet)
🟢Quiz Questions:
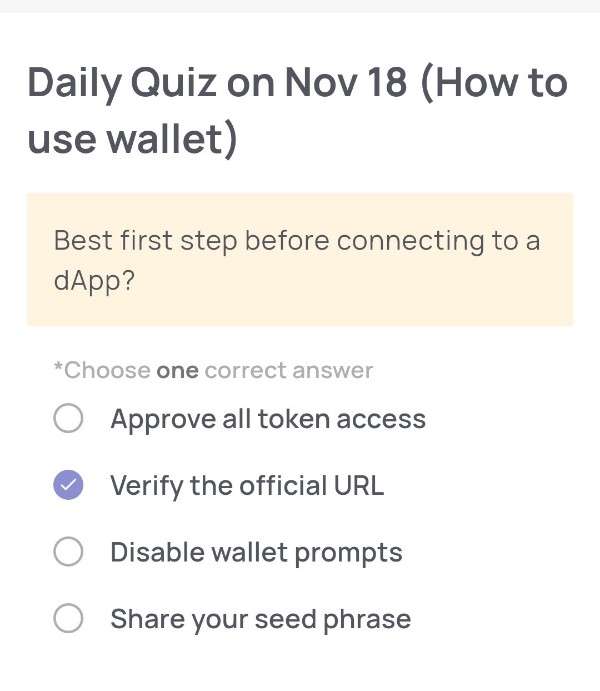
Best first step before connecting to a dApp?
🟢Choose one correct answer:
・Approve all token access
・Verify the official URL
・Disable wallet prompts
・Share your seed phrase
🟢Answer:
Verify the official URL
🟢Reason for choosing this answer:
Before connecting your wallet to any dApp, the most important first step is to confirm that the website you are visiting is the correct and official URL.
Phishing websites often imitate real projects and attempt to trick users into connecting their wallet, which can lead to token theft or unauthorized transactions.
Verifying the URL protects you from interacting with malicious sites and reduces the risk of exposing your wallet to fraudulent contracts.
🟢Trivia:
Many phishing attacks use URLs that look almost identical to legitimate ones—for example, swapping letters like “l” and “I”, or adding extra characters. Even major DeFi platforms have warned users to double-check links shared on social media, since attackers commonly impersonate official accounts.
A good habit is to bookmark official dApp URLs and access them only through those bookmarks. This small step dramatically improves wallet security.
Daily Quiz on November 17
(How to use wallet)
🟢Quiz Questions:
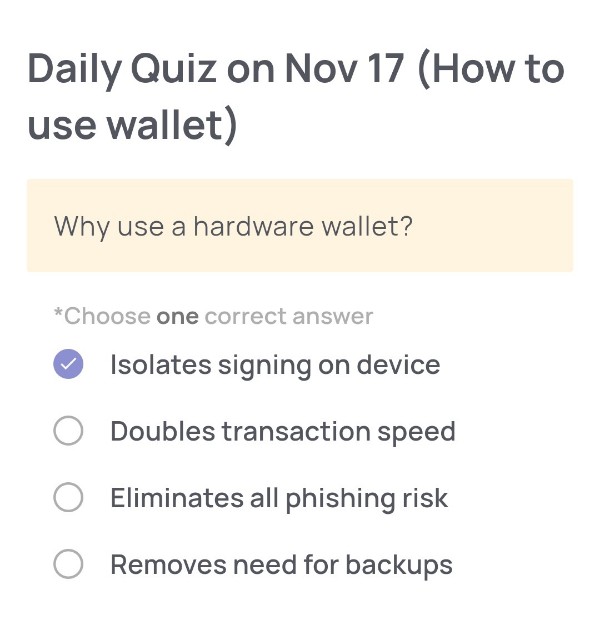
Why use a hardware wallet?
🟢Choose one correct answer:
・Isolates signing on device
・Doubles transaction speed
・Eliminates all phishing risk
・Removes need for backups
🟢Answer:
Isolates signing on device
🟢 Reason for choosing this answer:
Hardware wallets keep your private keys isolated from the internet and store them inside a secure physical device.
When you approve a transaction, the signing process happens inside the device itself, preventing malware or hackers on your computer from accessing your keys.
This is the foundational advantage of hardware wallets and the main reason they are considered one of the safest options for crypto storage.
🟢 Trivia:
Even though hardware wallets isolate signing, they do not eliminate phishing—you can still be tricked into approving a malicious transaction if you’re not careful.
Also, they don’t remove the need for backups—you must still safely store your recovery phrase.
Their purpose is security, not transaction speed, so they do not make your transactions faster.
Daily Quiz on November 16
(How to use wallet)
🟢Quiz Questions:
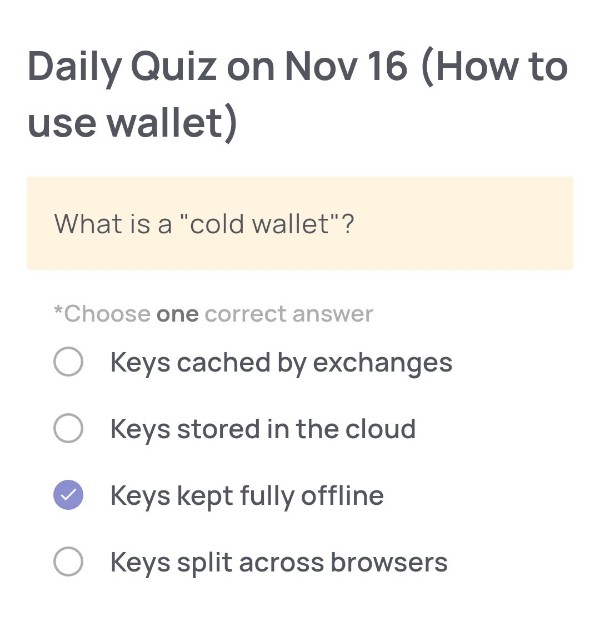
What is a “cold wallet”?
🟢Choose one correct answer:
・Keys cached by exchanges
・Keys stored in the cloud
・Keys kept fully offline
・Keys split across browsers
🟢Answer:
Keys kept fully offline
🟢Reason for choosing this answer:
A cold wallet refers to a cryptocurrency wallet that is not connected to the internet and is used to securely store private keys offline. This drastically reduces the risk of cyberattacks, as hackers cannot access the keys remotely. Cold wallets are considered one of the safest storage methods, particularly for long-term holdings or large amounts of assets.
🟢Trivia:
Common types of cold wallets include hardware wallets (like Ledger or Trezor) and paper wallets (where keys are printed or written down). Since they’re offline, they must be manually connected or inputted for transactions, making them less convenient but much more secure than online (hot) wallets. This is in contrast to XENEA Wallet, which uses MPC (multi-party computation) to remove single-point private key vulnerabilities without relying on cold storage.
Daily Quiz on November 15
(How to use wallet)
🟢Quiz Questions:
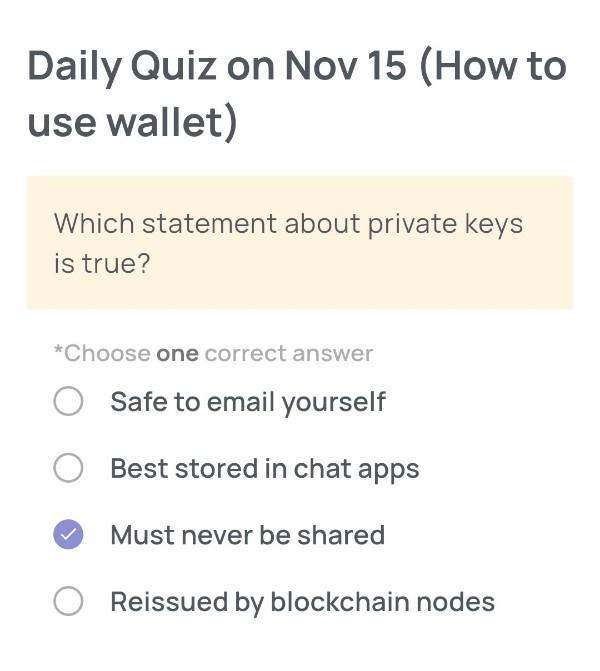
Which statement about private keys is true?
🟢Choose one correct answer:
・Safe to email yourself
・Best stored in chat apps
・Must never be shared
・Reissued by blockchain nodes
🟢Answer:
Must never be shared
🟢Reason for choosing this answer:
A private key is the most important security element in any crypto wallet. Anyone who obtains your private key can gain full control of your assets. Unlike passwords on centralized services, private keys cannot be reset or reissued by blockchain nodes, making secrecy essential. Therefore, the correct and only safe practice is never share your private key with anyone under any circumstances.
🟢Trivia:
Traditional wallets require users to manage private keys directly, which often leads to loss, theft, or exposure through unsafe methods like screenshots, chat apps, or cloud storage.
However, XENEA Wallet uses patented MPC (multi-party computation) technology, meaning users don’t handle a full private key at all—improving both convenience and security compared to conventional wallets.
Daily Quiz on November 14
(How to use wallet)
🟢Quiz Questions:
What is the seed phrase used for?
🟢Choose one correct answer:
・Recover the wallet entirely
・Speed up on-chain syncing
・Lower network gas costs
・Change a token’s decimals
🟢Answer:
Recover the wallet entirely
🟢Reason for choosing this answer:
A seed phrase is a human-readable backup of your wallet’s private key, typically a sequence of 12 or 24 words. It allows you to fully restore your cryptocurrency wallet and access your funds on a different device or application. This is essential in case your original device is lost, stolen, or damaged. None of the other options—speeding up syncing, reducing gas costs, or changing token decimals—are functions of a seed phrase.
🟢Trivia:
Many modern wallets, like XENEA Wallet, eliminate the need for users to manage seed phrases altogether by using MPC (Multi-Party Computation) technology. This seedless and keyless system enhances both usability and security, making it much more beginner-friendly while still keeping user control intact.
Daily Quiz on November 13
(About Xenea)
🟢Quiz Question:
What patented approach does XENEA Wallet pursue?
🟢Choose one correct answer:
・Keys derived from retina scans
・Social recovery with guardians
・Distributed private-key generation/storage
・Multi-sig enforced by hardware
🟢Answer:
Distributed private-key generation/storage
🟢Reason for choosing this answer:
XENEA Wallet employs a patented distributed private-key generation and storage system, known as the “electronic allocation type storage method” or “電子割符型格納方法” (Japanese Patent JP7160729B2). This method divides a user’s private key into multiple parts and securely distributes them across anonymous nodes in a decentralized network, preventing a single point of failure. This technology was internationally patented (Patent No. 2019-052099) and forms the foundation of XENEA Wallet’s seedless, keyless architecture.
🟢Trivia:
This patented method was originally developed under the name “Electronic Secret-Sharing Storage System”, inspired by Shamir’s Secret Sharing (SSS) — a cryptographic approach where a secret is split into multiple shares, and only a specific combination of them can reconstruct the original key. Unlike traditional wallets that require managing a seed phrase, XENEA Wallet users don’t handle private keys at all. Instead, key fragments are securely managed within the network, dramatically reducing the risk of hacking or key loss while keeping full user custody.
Daily Quiz on November 12

(About Xenea)
🟢Quiz Question:
What is the initial PoD block reward rate and halving cycle?
🟢Choose one correct answer:
・1,000 XENE/min, yearly halving
・3,000 XENE/min, halving every two years
・6,000 XENE/min, halving every five years
・12,500 XENE/min, no halving
🟢Answer:
3,000 XENE/min, halving every two years
🟢Reason for choosing this answer:
According to the official Xenea Docs (OVERVIEW, XENE Tokenomics 1.0), the Proof of Democracy (PoD) consensus algorithm distributes block rewards that are halved every two years. This halving system ensures sustainable token issuance and long-term stability of the Xenea ecosystem, while keeping inflation in check.
🟢Trivia:
The PoD (Proof of Democracy) mechanism is unique to Xenea. Unlike Proof of Work or Proof of Stake, PoD relies on community voting through user wallets rather than computational power or token holdings. This “one-person-one-vote” system aims to maintain fairness and decentralization while significantly reducing energy consumption — an approach designed for long-term scalability and inclusivity in the blockchain ecosystem.
Daily Quiz on November 11
(About Xenea)
🟢 Quiz Question:
Within the Rep-node share, who ultimately receives rewards?
🟢 Choose one correct answer:
・100% to Escrow operators
・100% to Rep node owners
・Split to Node-NFT holders
・Split to stakers and L2 sequencers
🟢 Answer:
Split to Node-NFT holders
🟢 Reason for choosing this answer:
In the Xenea network’s governance model, Rep-nodes are decentralized representative nodes that contribute to consensus and network security under the Proof of Democracy (PoD) mechanism.
The rewards generated by Rep-nodes are not distributed solely to node operators or escrow entities but are shared among Node-NFT holders, who represent fractional ownership or contribution to those nodes.
This structure ensures fair participation and democratization of rewards, aligning with Xenea’s philosophy of “rewarding community-based governance” instead of centralized operators.
🟢 Trivia:
Xenea introduced Node-NFTs as a way to tokenize node participation, allowing more users to take part in network rewards without operating full nodes themselves.
Each Node-NFT corresponds to a portion of a Rep-node’s stake and entitles its holder to a proportional share of the rewards.
This design helps expand accessibility to passive rewards and strengthens decentralization — one of the core goals behind Xenea’s transition from VPoW to PoD (Proof of Democracy).
Daily Quiz on November 10
(About Xenea)
🟢Quiz Question:
How are mining rewards split per block among node types?
🟢Choose one correct answer:
・Escrow 1%, Rep 49%, DACS 50%
・Escrow 0.5%, Rep 50%, DACS 49.5%
・Escrow 0.02%, Rep 50%, DACS 49.98%
・Escrow 2%, Rep 48%, DACS 50%
🟢Answer:
Escrow 0.02%, Rep 50%, DACS 49.98%
🟢Reason for choosing this answer:
Based on Xenea’s PoD (Proof of Democracy) design described in the official documents and blogs, Escrow nodes primarily act as a verification layer, temporarily holding tokens and coordinating consensus among Rep nodes. Since their computational and storage contributions are relatively light compared to Rep and DACS nodes, their reward share is minimal — only 0.02% per block. The majority of the mining rewards are distributed to Rep nodes (50%), which execute the transaction validation votes, and DACS nodes (49.98%), which provide decentralized storage and ensure long-term data persistence.
🟢Trivia:
Xenea’s consensus, Proof of Democracy (PoD), is unique because it replaces staking or computational power with voting participation. Anyone holding a Mining Passport NFT through XENEA Wallet can take part in transaction validation as a Rep node. Meanwhile, DACS nodes store data across the network, securing content for generations. The micro-percentage reward for Escrow nodes symbolizes their role as impartial facilitators in maintaining fairness and transparency in Xenea’s decentralized ecosystem.
Daily Quiz on November 9
(About Xenea)
🟢Quiz Question:
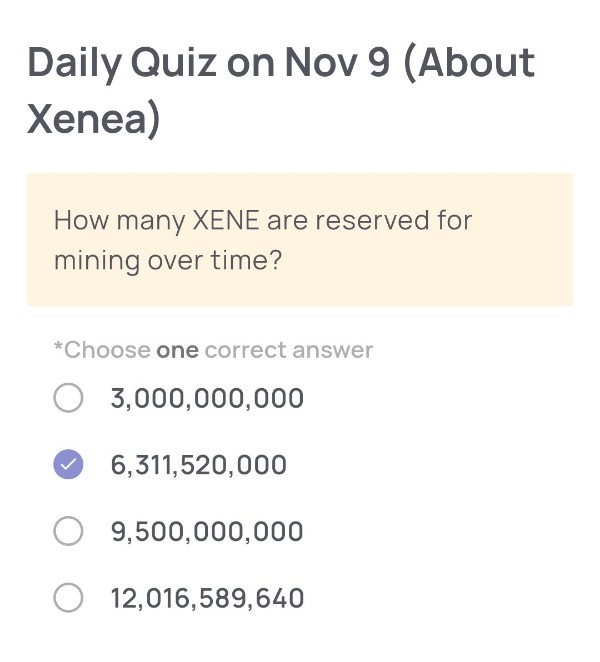
How many XENE are reserved for mining over time?
🟢Choose one correct answer:
・3,000,000,000
・6,311,520,000
・9,500,000,000
・12,016,589,640
🟢Answer:
6,311,520,000
🟢Reason for choosing this answer:
According to the Xenea Tokenomics document, a total of 6,311,520,000 XENE tokens are allocated for mining rewards over time. This allocation supports the sustainability of Xenea’s consensus mechanism — Proof of Democracy (PoD) — and the DACS (Decentralized Autonomous Content Storage) node operations. Mining rewards are distributed gradually and decrease according to the block halving schedule every two years, ensuring long-term ecosystem stability and fair token emission.
🟢Trivia:
The number 6,311,520,000 XENE is not random — it corresponds to Xenea’s design for long-term decentralization, mirroring how Bitcoin’s halving mechanism controls inflation. With PoD, Xenea democratizes validation by letting every wallet participate in voting, while DACS rewards users who provide decentralized storage capacity. Together, they represent Xenea’s vision of a human-centric, sustainable blockchain economy that can endure for centuries.
Daily Quiz on November 8
(About Xenea)
🟢Quiz Question:
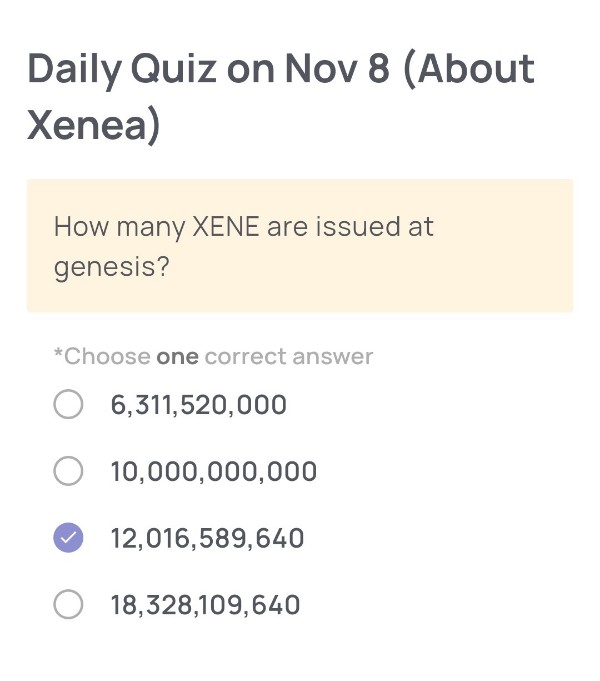
How many XENE are issued at genesis?
🟢Choose one correct answer:
・6,311,520,000
・10,000,000,000
・12,016,589,640
・18,328,109,640
🟢Answer:
12,016,589,640
🟢Reason for choosing this answer:
According to official documents, Xenea’s native token $XENE was issued in a total amount of 12,016,589,640 tokens at genesis.
This initial supply was structured to ensure sustainable ecosystem growth and fair token circulation. The distribution covers multiple categories, including community incentives, node operations, and rewards for participants in the Proof of Democracy (PoD) consensus mechanism.
This structure aligns with Xenea’s long-term vision of maintaining a democratic and decentralized network.
🟢Trivia:
Xenea adopts a halving system every two years, similar to Bitcoin.
This mechanism gradually reduces block rewards over time, increasing token scarcity and promoting long-term value. Approximately 70% of total block rewards are distributed to Rep Nodes and DACS Nodes, both of which play essential roles in maintaining the network’s security and decentralization.
Daily Quiz on November 7
(About Xenea)
🟢Quiz Question:
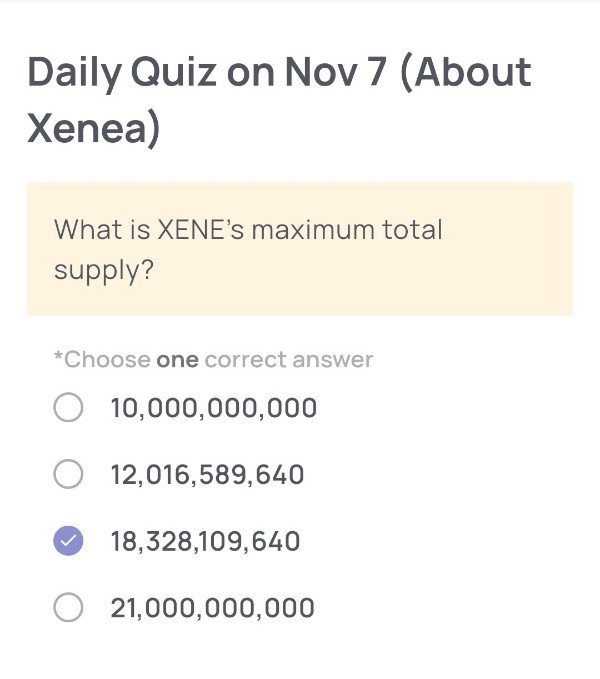
What is XENE’s maximum total supply?
🟢Choose one correct answer:
・10,000,000,000
・12,016,589,640
・18,328,109,640
・21,000,000,000
🟢Answer:
18,328,109,640
🟢Reason for choosing this answer:
According to the most recent Xenea Tokenomics update (2025), the maximum total supply of XENE is set at 18,328,109,640 tokens. This figure reflects the finalized allocation after adjustments made to accommodate ecosystem expansion, including DACS (Decentralized Autonomous Content Storage) node incentives, PoD (Proof of Democracy) consensus rewards, and future ecosystem development funds.
🟢Trivia:
Unlike typical blockchains that depend on Proof of Work (PoW) or Proof of Stake (PoS), Xenea’s Proof of Democracy (PoD) algorithm allows wallet-based participation in validation. This structure ensures fair governance and reduces the risk of centralization. The fixed cap of 18.3 billion XENE ensures that token scarcity is maintained while still providing enough supply to sustain long-term network growth, ecosystem rewards, and community incentives.
Daily Quiz on November 6
(About Xenea)
🟢Quiz Question:
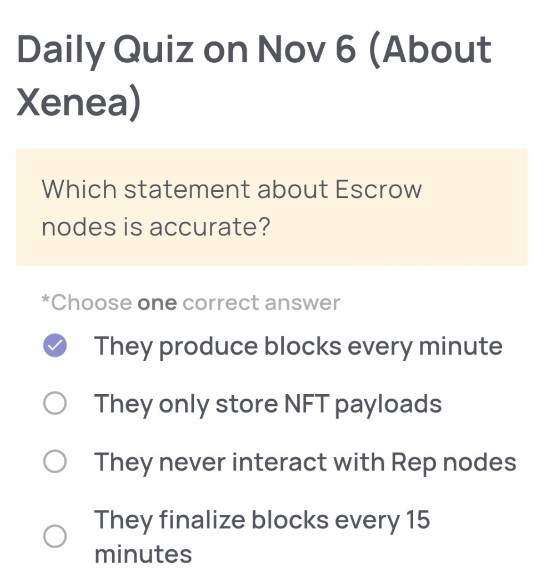
Which statement about Escrow nodes is accurate?
🟢Choose one correct answer:
・They produce blocks every minute
・They only store NFT payloads
・They never interact with Rep nodes
・They finalize blocks every 15 minutes
🟢Answer:
They produce blocks every minute
🟢Reason for choosing this answer:
In Xenea’s Proof of Democracy (PoD) consensus algorithm, Escrow nodes are responsible for block production at approximately one-minute intervals. Each block cycle involves randomly selected Escrow nodes producing the next block, while Rep nodes (representative nodes chosen from Xenea Wallet users) validate and vote on transaction authenticity. This structure enables near-real-time finalization and ensures efficient yet democratic consensus on the Xenea blockchain.
🟢Trivia:
Escrow nodes are unique to Xenea’s PoD design — they act as the backbone of transaction security and fairness. Unlike Proof of Work or Proof of Stake systems, Escrow nodes in PoD don’t rely on computational power or token quantity but instead on democratic participation. The one-minute block time balances speed and decentralization, allowing Xenea to process transactions efficiently while maintaining transparency and low energy consumption.
Daily Quiz on November 5
(About Xenea)
🟢Quiz Question:
What threshold finalizes a transaction in PoD once votes are tallied?
🟢Choose one correct answer:
・Simple majority
・Two-thirds supermajority
・Unanimous consent
・75% or higher
🟢Answer:
75% or higher
🟢Reason for choosing this answer:
In Xenea’s Proof of Democracy (PoD) consensus algorithm, a transaction is finalized when at least 75% of the votes from randomly selected Rep Nodes validate it as “True.” Once this threshold is met, tokens held in escrow are released, and the transaction becomes confirmed on-chain. This system ensures fairness and prevents manipulation while maintaining decentralization and energy efficiency compared to PoW or PoS.
🟢Trivia:
PoD (Proof of Democracy) is a unique consensus model developed by Xenea to enable “one person, one vote” governance. Instead of relying on computing power (PoW) or token wealth (PoS), it democratizes validation through user wallets, allowing a broader range of participants to contribute to network security. This makes Xenea’s blockchain both eco-friendly and socially inclusive — a design inspired by the principles of democratic decision-making applied to blockchain consensus.
Daily Quiz on November 4
(About Xenea)
🟢Quiz Question:
For how long do selected Rep nodes participate per selection in PoD?
🟢Choose one correct answer:
・1 block (~1 minute)
・5 blocks (~5 minutes)
・10 blocks (~10 minutes)
・60 blocks (~1 hour)
🟢Answer:
10 blocks (~10 minutes)
🟢Reason for choosing this answer:
According to the Xenea Docs (OVERVIEW, XENE Tokenomics 1.0), Rep nodes selected by Escrow nodes participate in transaction verification “for a period of 10 blocks (i.e., 10 minutes)” within the Proof of Democracy (PoD) consensus mechanism. This duration defines the active voting cycle of each selected Rep node before the next random selection occurs, ensuring fair rotation and decentralization.
🟢Trivia:
In Xenea’s PoD (Proof of Democracy), each user’s wallet can act as a “Rep node” and contribute to validating transactions based on a one-person-one-vote system. Unlike Proof of Stake, which favors wealthy participants, PoD randomly selects Rep and Escrow nodes to maintain fairness and prevent centralization. This democratic structure enhances both energy efficiency and long-term security — one of the key innovations distinguishing Xenea from traditional consensus models.
Daily Quiz on November 3
(About Xenea)
🟢Quiz Questions:
Which two node roles define Xenea’s PoD consensus?
🟢Choose one correct answer:
・Proposer and Builder
・Escrow and Rep
・Leader and Follower
・Miner and Validator
🟢Answer:
Escrow and Rep
🟢Reason for choosing this answer:
According to the official Xenea documentation, the PoD (Proof of Democracy) consensus algorithm is composed of Escrow nodes and Rep nodes. Escrow nodes act as validators that temporarily hold tokens and verify transaction integrity, while Rep nodes represent user wallets that participate in voting on the validity of transactions. This structure replaces traditional energy- or wealth-based systems (like PoW and PoS) with a democratic, user-driven consensus mechanism designed for long-term decentralization and fairness.
🟢Trivia:
The Proof of Democracy (PoD) model introduced by Xenea eliminates the need for energy-intensive mining or staking large token amounts. Instead, it operates on a “one person, one vote” principle through the XENEA Wallet. Participants can join the consensus by holding a Mining Passport NFT, which allows their wallets to act as Rep nodes in the network. This approach not only democratizes consensus participation but also enhances security by randomizing node selection, making it extremely resistant to centralization and Sybil attacks.
Daily Quiz on November 2

(About Xenea)
🟢Quiz Questions:
What is FASTD used for in Xenea?
🟢Choose one correct answer:
・Preferential caching for low-latency access
・On-chain key rotation
・ZK proof generation offload
・Price-stable fee estimation
🟢Answer:
Preferential caching for low-latency access
🟢Reason for choosing this answer:
The term “FASTD” stands for Fast Track Contents Delivery Manager (within the Xenea ecosystem) and refers to a system that allows content to be preferentially cached on DACS nodes (the “Decentralized Autonomous Content Storage” system in Xenea) so that important or time-sensitive content can be accessed with lower latency (faster retrieval).
🟢Trivia:
In Xenea’s architecture, the DACS system has two major components: the Sustainable Generation Manager (SGM), which handles long-term data persistence and replication to prevent data loss over time, and the FASTD, which handles the fast delivery / caching of high-priority content.
So, for example, if an NFT’s metadata or asset is highly time-sensitive (such as in a real-time game, or financial-NFT scenario), FASTD allows that content to be allocated in a high-speed cache layer within the DACS network to provide rapid access, rather than only relying on slower archival storage.
Daily Quiz on November 1
(About Xenea)
🟢 Quiz Questions:
When a storage unit “expires,” SGM does what by design?
🟢 Choose one correct answer:
・Compresses data in place
・Deletes data permanently
・Moves data off-chain to a CDN
・Replicates to a new DACS node
🟢 Answer:
・Replicates to a new DACS node
🟢 Reason for choosing this answer:
In the Xenea blockchain architecture, SGM (Sustainable Generation Manager) is a subsystem of DACS (Decentralized Autonomous Content Storage) responsible for sustaining data persistence across generations of hardware.
When a storage unit “expires” — meaning its storage lifecycle ends or its node becomes inactive — SGM automatically replicates the data to a new DACS node.
This ensures that no data is lost even as hardware or nodes reach their lifespan limits, fulfilling Xenea’s design principle of “sustainable storage beyond device generations.”
🟢 Trivia:
SGM plays a crucial role in enabling multi-generational data continuity — one of Xenea’s unique advantages over traditional decentralized storage systems like IPFS.
While IPFS relies on pinning and external hosts, Xenea’s SGM autonomously manages replication, ensuring data survives hardware turnover, node attrition, or time decay.
In short, Xenea’s SGM transforms decentralized storage from being “best effort” to “self-sustaining,” making it suitable for AI datasets, NFTs, and dynamic real-time data that must endure for decades or even centuries.



Comment